Monday, April 29, 2013
How to Enable Netmeeting in Windows XP?
Net meeting is used for the remote sharing of desktop.The main advantage of using this technique is that you can also transfer files, Using Headphones and mic you can also communicate.Another advantage is that there is no need to install any third party software and the control remains to both the users simultaneously.here are some simple steps to activate net meeting in Windows XP based PC:
and enter conf Command as shown below an hit enter
and enter conf Command as shown below an hit enter
Sunday, April 28, 2013
DBMS Languages
DBMS Support a variety of users and provides appropriate languages and interface or each category of users.Here are some languages that are provided by DBMS:
1) Data Definition Language (DDL): This Language is used define data structures and specially database schemas. these statements are used to create, alter, or drop data structures. ALTER ,CREATE ,DROP are some examples of DDL.
2) Storage Definition Language (SDL): This language is used to define internal schema. It defines that what will be the Physical structure of database, How many bites per field will be used, what will be the order of fields, and how records will be accesses etc.
1) Data Definition Language (DDL): This Language is used define data structures and specially database schemas. these statements are used to create, alter, or drop data structures. ALTER ,CREATE ,DROP are some examples of DDL.
2) Storage Definition Language (SDL): This language is used to define internal schema. It defines that what will be the Physical structure of database, How many bites per field will be used, what will be the order of fields, and how records will be accesses etc.
Database Independence
"The ability to change the Schema at one level of database system without having to change the Schema at the next higher level is called data independence". Data Independence is divided into two categories:
1) Logical Data Independence: It is the ability to change conceptual schema without making any changes to application programs or external schema. In Logical data Independence new rows and columns are added without changing user views and programs.it is more difficult to achieve rather than Physical Data Independence.
2) Physical Independence: It is the ability to change internal schema without making any changes to conceptual schema.Hence there is no need to change the external schema.Physical data independence hides all details of storage structure from user applications. Modifications at physical level improves performance and any new change is absorbed by the mapping techniques.
1) Logical Data Independence: It is the ability to change conceptual schema without making any changes to application programs or external schema. In Logical data Independence new rows and columns are added without changing user views and programs.it is more difficult to achieve rather than Physical Data Independence.
2) Physical Independence: It is the ability to change internal schema without making any changes to conceptual schema.Hence there is no need to change the external schema.Physical data independence hides all details of storage structure from user applications. Modifications at physical level improves performance and any new change is absorbed by the mapping techniques.
DBMS Users
It is very difficult to design and maintain large databases for a single user.To perform such activities no. of users are involved .These users are called DBMS users and can be categorized as:-
1) Database Administrator: DBA is a person that performs installation, configuration, up gradation monitoring and maintenance of databases in an organization.He is also responsible for the database recovery and security.
2) Database Designers: Database designers are responsible for data identification that is to be stored and choosing database structure that represents and stores this data.They communicate with the user and designs database as per their requirements. They creates Tables, Indexes, Views, Constraints, Triggers, Storage Parameters etc.
1) Database Administrator: DBA is a person that performs installation, configuration, up gradation monitoring and maintenance of databases in an organization.He is also responsible for the database recovery and security.
2) Database Designers: Database designers are responsible for data identification that is to be stored and choosing database structure that represents and stores this data.They communicate with the user and designs database as per their requirements. They creates Tables, Indexes, Views, Constraints, Triggers, Storage Parameters etc.
Thursday, April 25, 2013
Semaphores
These are like integers but has the following three difference from them:
1) Its value can be initialized as integer but only increment or decrement operations are allowed and its current value can't be read.
2) If any thread decrements its value and result is negative then thread itself can't continue until any other thread increments the Semaphore.
3) If any thread increments Semaphore and their are another threads waiting ,one of the thread gets blocked which was in waiting list.
1) Its value can be initialized as integer but only increment or decrement operations are allowed and its current value can't be read.
2) If any thread decrements its value and result is negative then thread itself can't continue until any other thread increments the Semaphore.
3) If any thread increments Semaphore and their are another threads waiting ,one of the thread gets blocked which was in waiting list.
What is Process?
Any Program that is under execution is called a Process e.g. scanning an image is a process.
For the completion of a process resources are required. These resources are allocated to process either when process is created or is under execution. For Example you have typed a page in Microsoft Word and you want to print it, as you give print command the print process is created and it requires Printer as resource. If any other process is using the printer then your page will be queued and will be printed when first process of printing is complete. A process may have sub processes which are called child processes.A Process can demand only those resources which are available e.g. if 8 resources are available than process can demand all 8 resources but 9th resource can't be demanded.
For the completion of a process resources are required. These resources are allocated to process either when process is created or is under execution. For Example you have typed a page in Microsoft Word and you want to print it, as you give print command the print process is created and it requires Printer as resource. If any other process is using the printer then your page will be queued and will be printed when first process of printing is complete. A process may have sub processes which are called child processes.A Process can demand only those resources which are available e.g. if 8 resources are available than process can demand all 8 resources but 9th resource can't be demanded.
Wednesday, April 24, 2013
Round-Robin Scheduling
It is the CPU Scheduling Technique specially designed for the time shared systems. This Technique is similar to FCFS Technique but the difference is that processes are switched at a regular interval of time and the regular internal is called time quantum.The can be from 0 to 100 milliseconds.
The ready queue is used in a circular fashion. The CPU is allocated to each process for a regular interval of time of 1 time quantum each new process is added to the tail ready queue. CPU scheduling picks first process from ready queue, set a timer to interrupt after 1 time quantum and then process is dispatched.If the burst time of process is less than a time quantum then it will automatically release the CPU.The average waiting time a round Robin policy is often high.
The ready queue is used in a circular fashion. The CPU is allocated to each process for a regular interval of time of 1 time quantum each new process is added to the tail ready queue. CPU scheduling picks first process from ready queue, set a timer to interrupt after 1 time quantum and then process is dispatched.If the burst time of process is less than a time quantum then it will automatically release the CPU.The average waiting time a round Robin policy is often high.
Priority Scheduling
It is a CPU Scheduling Technique in which CPU is allocated to the process with highest priority. Equal priority processes are served in FCFS order.Priority is indicated by fixed range of numbers, it can be 0 to 10 or 0 to 1000. However there is no protocol that whether 0 will be highest priority or lowest. Some systems used lower numbers as lower priority and some systems uses lower numbers as highest priority.
Consider the following set of processes assumed to arrive at 0 in the order P1, P2 and P3 with the CPU Burst time in milliseconds.
Process Burst time Priority
P1 10 3
P2 5 1
P3 6 2
Consider the following set of processes assumed to arrive at 0 in the order P1, P2 and P3 with the CPU Burst time in milliseconds.
Process Burst time Priority
P1 10 3
P2 5 1
P3 6 2
Shortest Job First (SJF) CPU Scheduling
It is a CPU Scheduling Technique in which CPU is allocated to the process whose burst time is minimal.
Consider the following set of processes with the length of the CPU burst given in millisecond.
Process Burst time
P1 10
P2 5
P3 1
P4 4
Consider the following set of processes with the length of the CPU burst given in millisecond.
Process Burst time
P1 10
P2 5
P3 1
P4 4
First Come First Serve (FCFS) CPU Scheduling
It is the simplest CPU scheduling algorithm in which CPU is allocated first to the process that request it first. This policy is managed by FCFS queue. When CPU is free it is allocated to the first process of the ready Queue and the running process is removed from the ready queue. The code generation for FCFS algorithm is simple. The main draw back of this technique is that average waiting time of a process is quite long.Consider the Following queue of process.
Process Burst Time
P1 10
P2 40
P3 1
Process Burst Time
P1 10
P2 40
P3 1
Hard Disk Drive (HDD)
It is a data storage device and is made up of a thin circular discs, called "Platters", which are coated on both the sides by Magnetic Material. A Disk pack may consist of number of Platters and are mounted on a central shaft that rotates them in same direction with same speed.The Data is written or accessed in a random manner and individual blocks of data can be stored or retrieved in any order rather than just sequentially.It is connected to computer using different interfaces such as IDE, SATA or SCSI.
Information Storage: In HDD information is stored on all surfaces of platters except upper and lower surface of top and bottom platters respectively. thus,a disk with 5 disk platters will have 8 recording surfaces. Each plotter is consist of no. of invisible concentric circles which are called tracks. A set of such corresponding tracks in all the surfaces is called cylinder. Tracks are further divided into sectors. * bit EBCDIC code is used for the information storage.The Information is stored in form of invisible magnetic spots. The Presence of magnetic spot represents binary 1 and absence represents binary 0.
Information Storage: In HDD information is stored on all surfaces of platters except upper and lower surface of top and bottom platters respectively. thus,a disk with 5 disk platters will have 8 recording surfaces. Each plotter is consist of no. of invisible concentric circles which are called tracks. A set of such corresponding tracks in all the surfaces is called cylinder. Tracks are further divided into sectors. * bit EBCDIC code is used for the information storage.The Information is stored in form of invisible magnetic spots. The Presence of magnetic spot represents binary 1 and absence represents binary 0.
Tuesday, April 23, 2013
OCR (Optical Character Reader)
This Device is used to detect alphabetic and numeric
characters that are printed on the paper. These Characters can be handwritten
or typed. These words must follow a standard size and no style should be used.
If characters are typed than they must be typed using special OCR fonts. The
standard OCR fonts are: OCR-A (American Standard) and OCR-B (European Standard).
Working: Once the whole Character is scanned it is compared with recognized standard character patterns. If the character matches or nearly matches it is considered that character is read. If the character does not match it is rejected.Fig. given below shows a handheld character reader.
Working: Once the whole Character is scanned it is compared with recognized standard character patterns. If the character matches or nearly matches it is considered that character is read. If the character does not match it is rejected.Fig. given below shows a handheld character reader.
Floppy Disk
It is a Magnetic type secondary storage media.It is Composed of a thin magnetic disk encapsulated in a rectangular plastic cover lined with fabric that is used to remove dust particles.They came in different sizes i.e. 8-Inch, 5.25-Inch and 3.5 Inch.The 8-Inch and 5.25-Inch floppy disks are obsolete now and only 3.5 Inch floppy is used rarely for the emergency start up of system or to update firmwares.Fig(1) given below shows a 3.5 Inch Floppy disk and various Parts of it.It mainly consist of Following Parts:
i)A hub that engages with drive motor
ii) A hole that identifies its capacity.
iii)A Shutter for protection,when removed from computer.
iv)A Plastic Housing
v)two polyester sheet to sandwich the magnetic disk in the middle to reduce friction.
vi)Magnetic coated plastic disk.
vii)A write Protection notch.
i)A hub that engages with drive motor
ii) A hole that identifies its capacity.
iii)A Shutter for protection,when removed from computer.
iv)A Plastic Housing
v)two polyester sheet to sandwich the magnetic disk in the middle to reduce friction.
vi)Magnetic coated plastic disk.
vii)A write Protection notch.
OMR (Optical Mark Reader)
It is a device that is used to read marked data from document forms such as tests or surveys.Some OMR devices uses dedicated scanner.It consist of a light source and light detector.When light falls on the paper it reflects it.Intensity of reflected light is more where paper is blank whereas darken areas of paper reflects less light.
In some OMR trans optic papers are used.when light is passed through paper,the intensity of light received at another end is low from darken areas and intensity is high from blank areas of paper.This combination of high low intensity is converted into binary values.OMR has the advantage that unlike OCR no complicated pattern recognition engine is required.Marks are constructed in such a way that their is no chance of error.

In some OMR trans optic papers are used.when light is passed through paper,the intensity of light received at another end is low from darken areas and intensity is high from blank areas of paper.This combination of high low intensity is converted into binary values.OMR has the advantage that unlike OCR no complicated pattern recognition engine is required.Marks are constructed in such a way that their is no chance of error.

Monday, April 22, 2013
Computer Generations
First Generation(1942-1955)
This Generation is considered to be form 1942-1955. These Machines were designed with the help of vacuum tubes. The main features of this Generation Computer were:
1. Were designed with vacuum tube’s which was only electronic component available during those days.
2. These computers were fastest of their time and could perform calculations in milliseconds.
3. They were bulk in size due to the use of thousands of vacuum tubs.
4. These devices were non-potable and were more frequent to failure.
This Generation is considered to be form 1942-1955. These Machines were designed with the help of vacuum tubes. The main features of this Generation Computer were:
1. Were designed with vacuum tube’s which was only electronic component available during those days.
2. These computers were fastest of their time and could perform calculations in milliseconds.
3. They were bulk in size due to the use of thousands of vacuum tubs.
4. These devices were non-potable and were more frequent to failure.
Characteristics of Computers
1) Speed: Computer is a very fast device it is capable of performing calculations in a few seconds that a human can do in entire month.
2) Accuracy: This is another Characteristic of computer that it performs all calculations with high accuracy. But this accuracy is dependent on its design and programming. If programming error occurs then result will also be affected by that.
3) No IQ: It is not a magical device and can perform only those tasks for which it is programmed or designed. But if it is designed with high class design then it can perform task with unthinkable speed and accuracy
4) No Feelings: Computers is an electronic device and is free from feeling. Though human designed Memory but it can’t be equivalent to human heart. It will work in any situation, any time.
5) High Storage Capacity: Computer can store large amount of data on single chip that can take entire building in printed form. This data can be accessed/ searched in a few seconds.
6) Versatile: It is another Important feature of computer it can perform multiple tasks in the same time e.g. while listening music you can access internet also.
7) Non-Stop working: Computers can be used in 24 X 7 working environment and is totally fatigue free.
2) Accuracy: This is another Characteristic of computer that it performs all calculations with high accuracy. But this accuracy is dependent on its design and programming. If programming error occurs then result will also be affected by that.
3) No IQ: It is not a magical device and can perform only those tasks for which it is programmed or designed. But if it is designed with high class design then it can perform task with unthinkable speed and accuracy
4) No Feelings: Computers is an electronic device and is free from feeling. Though human designed Memory but it can’t be equivalent to human heart. It will work in any situation, any time.
5) High Storage Capacity: Computer can store large amount of data on single chip that can take entire building in printed form. This data can be accessed/ searched in a few seconds.
6) Versatile: It is another Important feature of computer it can perform multiple tasks in the same time e.g. while listening music you can access internet also.
7) Non-Stop working: Computers can be used in 24 X 7 working environment and is totally fatigue free.
Bus (Computing)
CPU is connected to I/O and devices and memory by a group of lines these lines are called as Buses. There are three types of buses that are used in computer system.
1) Address Bus: This Bus carries the Address of I/O device or Memory that CPU wants to access. Address bus can be 8 bit, 16 bit or more. A system with n address lines can reference 2n address locations. This bus is a unidirectional bus and is also called A-Bus.
Friday, April 19, 2013
Direct Memory Access (DMA)
Data transfer between I/O devices and memory is slow due to
the speed mismatch in their speeds. This is avoided by removing the CPU from
the path and letting the peripheral device manage the memory buses directly. This “data transfer between I/O device and memory
without the involvement of CPU is called Direct Memory Access or DMA”.
In this type of data transfer CPU remains free for another
processes and has no control of the memory buses. In DMA CPU make use of two control signals
i.e. Bus Request (BR) and Bus Grant (BG). BR signal is used by the DMA controller to request the CPU for the
control of buses. When this signal is active, CPU terminate the current
execution of instruction and places data
bus, address bus, and read and write lines into high impedance state. This high
impedance state works like open circuit and output is disconnected.BG Signal is used by the CPU to inform
that all buses are now in high impedance state and the DMA controller can take
the control of buses.
Thursday, April 18, 2013
Cache Memory
It is the smallest and the fastest memory which stores
copies of data from most frequently used main memory locations. It is very near
to Processor or even in the Processor. The main idea behind the use of Cache
memory is to reduce average time to access memory. Its speed approaches to the
speed of CPU components.
Operation: -Whenever CPU wants to access the main memory, it
first looks the Cache Memory. If the word is found in the Cache then it is read
from there. But if the word is not found in Cache it is read from the main
memory. Block of word that is read from main memory is transferred to cache
memory .Only those words are kept in Cache that are most frequently used.
Pipelining
It is the Process in which sequential task is decomposed
into sub operations. Each sub operation is executed in a special dedicated
segment which is concurrently operates with all other segments. In Pipelining
result obtained from one segment is transferred to next segment of the Pipeline.
To get the final result the data is passed through all segments. This Process
looks like the flow of data in pipes hence named Pipelining. In Pipelining several
segments performs several computations at the same time. The overlapping of
computation is made possible by associating a register with each segment.
Isolation between each segment is provided by the registers so that each can
operate on distinct data simultaneously.
Difference Between Testing and Debugging
S. No.
|
Testing
|
Debugging
|
1
|
It is a Process in
which a Program is validated.
|
It is the Process in
which program errors are removed.
|
2
|
It is a Positive
activity that demonstrates that Program is correct and meets its design
specifications.
|
It is a negative
activity in which known errors or bugs are removed.
|
3
|
Testing finishes when
all verifications against desired specifications have been done.
|
Debugging Finishes when
all known errors are removed. |
Wednesday, April 17, 2013
Functions of Operating System
1) Process Management: - Operating System allocates resources to Processes,
enable processes to share and exchange information, protect the resources of
each process from other processes and enable synchronization among processes. Deadlock
avoidance and recovery is also function of Operating System.
2) Input / Output Management:-Assignment of various input and output devices to one or more programs is done by the operating system.
3) Memory Management: - Allocation of main memory and secondary memory to the system programs as well as user data is done by the Operating System.
4) File Management:-How files will be transferred from one device to another and how they will be saved or accessed is managed by the Operating System
5) Determine and maintain order of Jobs: - It is the Responsibility of the Operating System to decide that jobs will be completed in which order. It decides that first preference should be given to which request and which can be delayed.
2) Input / Output Management:-Assignment of various input and output devices to one or more programs is done by the operating system.
3) Memory Management: - Allocation of main memory and secondary memory to the system programs as well as user data is done by the Operating System.
4) File Management:-How files will be transferred from one device to another and how they will be saved or accessed is managed by the Operating System
5) Determine and maintain order of Jobs: - It is the Responsibility of the Operating System to decide that jobs will be completed in which order. It decides that first preference should be given to which request and which can be delayed.
Tuesday, April 16, 2013
FSK (Frequency Shift Keying)
It is the Modulation Technique in which Amplitude and Phase
of Signal are kept Constant while frequency is varies to represent binary 1 or
0.One level of frequency represents binary 1 and other represents binary 0.The
main advantage of using this technique is that it is less prone to noise and
sender is only concerned about
the frequency and not about the amplitude.
How to Clone Disks?
Its not possible to install every machine if you want to install them in bulk in lesser time.and if you install them one by one than it is a time consuming process.Another alternate is to clone the disks.This technique is only useful when you want to install machines with same software's , same configurations.To do so one of the most popular software is Acronics True Image Home.
before performing clone install a fresh machine with all configurations and application software's or you may copy an existing machine.The main Advantage of using this software is that it is very fast.
Here are Some simple steps that are used in Acronics True Image.
STEP1-->Download and Install Acronics True Image Home from Official website of Acronics.
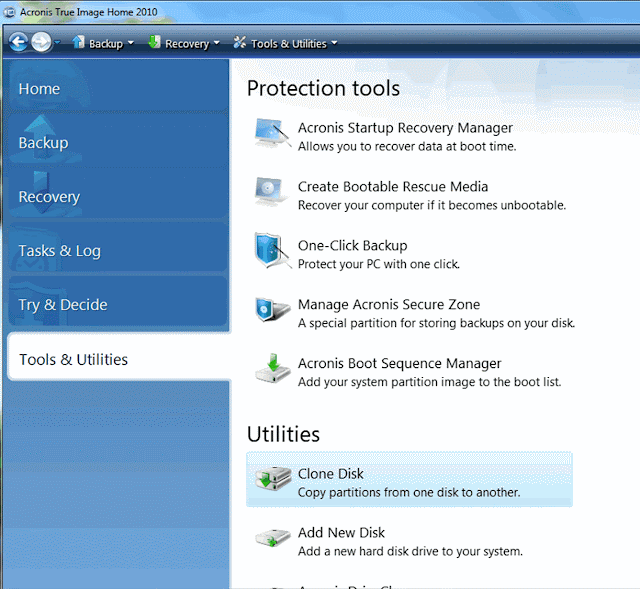
STEP2-->Open Acronics True Image ,click on Tools and utilities and select clone disks.
before performing clone install a fresh machine with all configurations and application software's or you may copy an existing machine.The main Advantage of using this software is that it is very fast.
Here are Some simple steps that are used in Acronics True Image.
STEP1-->Download and Install Acronics True Image Home from Official website of Acronics.
STEP2-->Open Acronics True Image ,click on Tools and utilities and select clone disks.

Monday, April 15, 2013
Drive not opening on double click
Many time it happens that when you open any drive of your Computer,it Does not Open Directly and gives out a choice to open with program.This Problem can be resolved by the use of a Software Called Combo fix without formatting the Hard Disk Drive.It is a free utility .(Click Here To Download).Figure given below illustrates the screen that appears to you when you double click any partition of your HDD.
Thursday, April 11, 2013
Difference Between Structure and Union
Characteristics
|
Structure
|
Union
|
Definition
|
A structure is a collection of variables under a single name. These variables can be of different types, and each has a name which is used to select it from the structure.
|
A union is a special data type that enables to store different data types in the same memory location. You can define a union with many members, but only one member can contain a value at any given time
|
Declaration
| typedef struct {
char name[64];
char course[128];
int age;
int year;
} student;
| union Data { int i; float f; char str[20]; } data; |
Amplitude Shift Keying (ASK)
Amplitude Shift Keying (ASK) is a Modulation technique that is used in Digital to analog Conversions. This technique uses strength of signal to represent binary 0 or 1 value.in this only amplitude changes while frequency and phase both are kept constant.it uses finite number of amplitudes, each assigned a unique pattern of binary digits that represents binary 1 or 0.
The main Disadvantage of this technique is that unwanted energy or noise from other sources may vary signal amplitude and can change original sent value. Another problem is that Transmission speed is dependent on the physical characteristics of the transmission media.
Wednesday, April 10, 2013
Network Protocols and Their Functions
Protocols
Whenever a person want to talk with another person then their communicating language should be same so that they can easily communicate with each other .If they will use different languages then they can not understand what the other is saying. Similarly in Computer Networks certain rules are defined so that computers can communicate with one another.These Pre defined rules are called Protocols and can be defined as "Protocols are the predefined rules between the communicating devices that govern the communication between them."Functions Of Protocols
i) Sequencing of Data:- Protocols split large size messages to equal size pieces called Packets which can be transmitted easily.each packet contains unique identification number and can be easily arranged at receiver end to create original message.
ii) Flow Control of Data:-This is another important function of protocols.if sender is sending continuously data and receiver is not in a condition to receive that data or having less receiving speed then their are the chances of data loss.This data loss is avoided by the use of Protocols.
Problems Associated with Wired Media
Attenuation
With The increase in the distance the energy of signal decreases.This energy loss is called Attenuation.This Energy loss is due to the Resistance of the Transmission wire which gets warm when signals are passed through them.This energy loss is Frequency Dependent.To re-boost these weak signals amplifiers are used and signal can travel long distance.Tuesday, April 9, 2013
Identification of Computer Ports
Port Name | Used for Connecting | Looks Like |
PS/2 | Keyboard/Mouse | |
RS-232 or Communication Port or Serial Port | Used to Connect Serial Devices Such as Modem, Passbook Printer, KIOSK Machine, Ticket Machine etc. | |
LPT Port | Used to Connect Printer or Parallel Interface Devices. | |
VGA Port | Used to Connect Monitor or TFT /LCD | |
USB Ports | Used to Connect USB Devices | |
Ethernet Port | Used to Connect LAN or Network | |
HDMI Port(High Definition Multimedia Interface) | Single Multimedia Output Interface that incorporates high quality audio/video output for HD TVs and Monitors. | |
S- Video( Known as Super Video) | It uses two different signal lines for luminance and Chroma. It does not carry audio on same cable and can support resolution up to 576i .Mainly used in Digital Cam coders, DVD- Players and Graphics Cards. | |
DVI (Digital Video Interface) | Output port that gives digital output and mainly used in LCD monitors. | |
Display Port | It’s very Similar to HDMI port but its data transfer rate is High. |
Monday, April 8, 2013
Open Suse 12.2 Installation Step by Step
1) Minimum Hardware Requirements
When you’re ready, insert the DVD and (re)start the computer. Live CD/USB installation is described below
The first thing you’ll see is this welcome screen.

- CPU: Pentium III 500 MHz or higher processor (Pentium 4 2.4 GHz or higher or any AMD64 or Intel64 processor recommended)
- RAM: 1 GB physical RAM (2 GB recommended)
- Disk Space: 5.0 GB for a normal installation (more recommended)
- Sound and Graphics Card: Most modern cards are supported
When you’re ready, insert the DVD and (re)start the computer. Live CD/USB installation is described below
The first thing you’ll see is this welcome screen.

Sunday, April 7, 2013
Thursday, April 4, 2013
How to Test Earthing Using Digital Multimeter
Some time when you touch your monitor or CPU at home it gives you Electrical shock like feeling or even full Electrical shock. The Reason behind this is that most of the houses are not earthed.
Here are some simple steps to test Earthing in your home or at any organization->
Step1-->Set Your Digital Multimeter to AC testing Mode and set Max. Voltage to 750V
Subscribe to:
Posts (Atom)